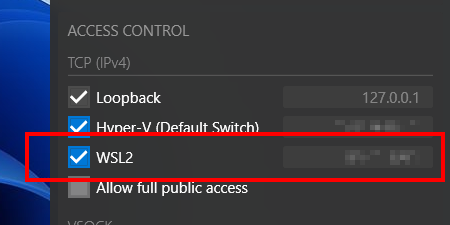
Starting from X410 version 3.0.0, X410 has a built-in feature that automatically blocks external TCP connections and only allows TCP connections from WSL2. Hence, you no longer have to set up separate inbound rules as described below; you simply need to enable the new WSL2 option in X410 and have your computer securely protected.
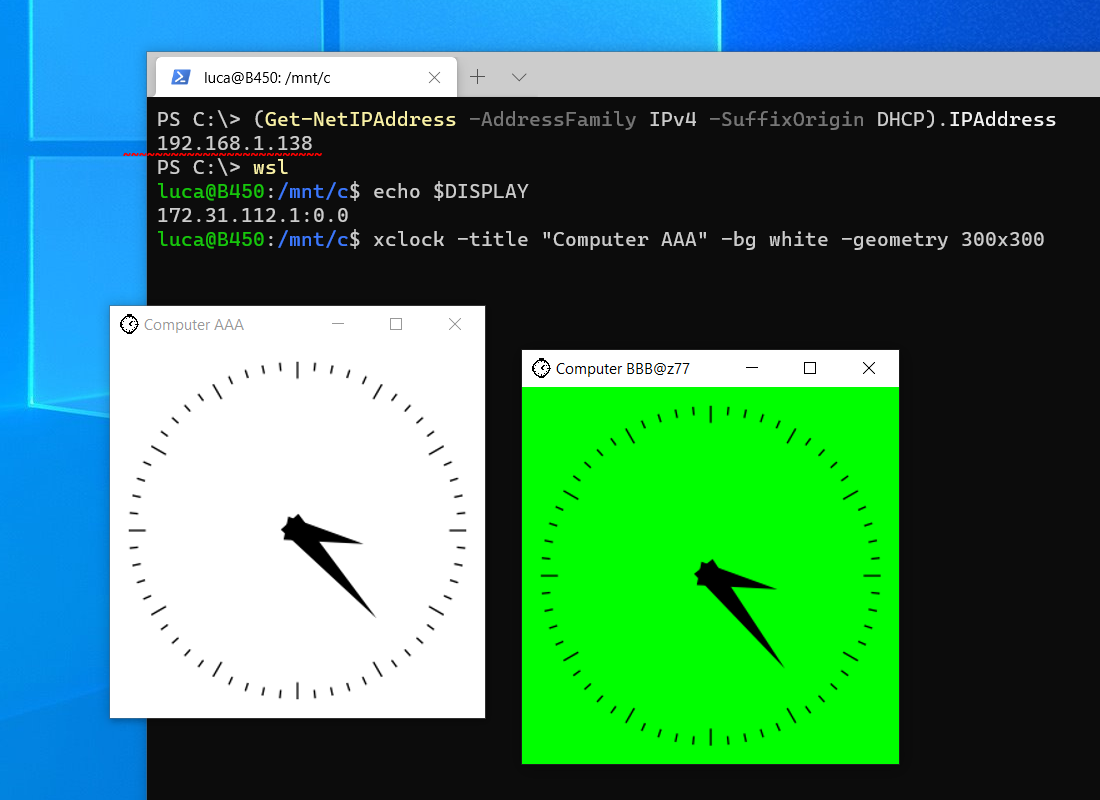
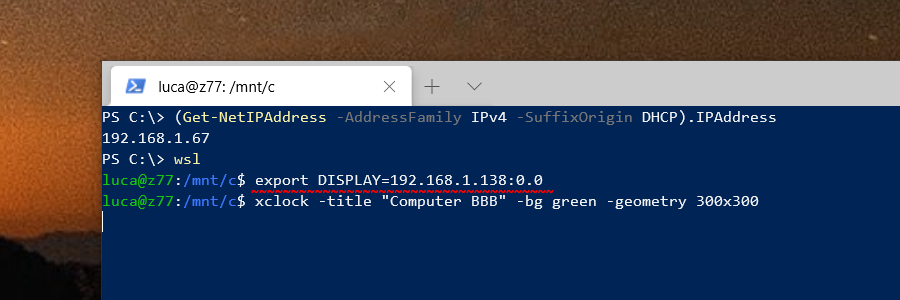
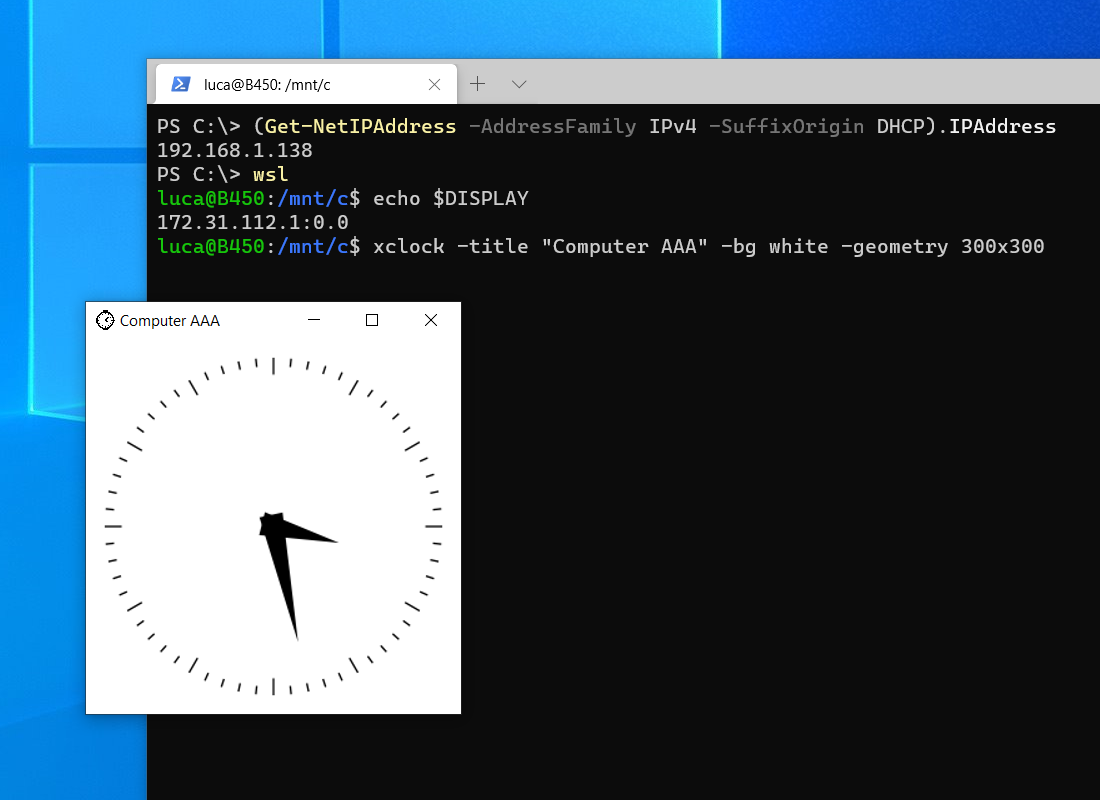
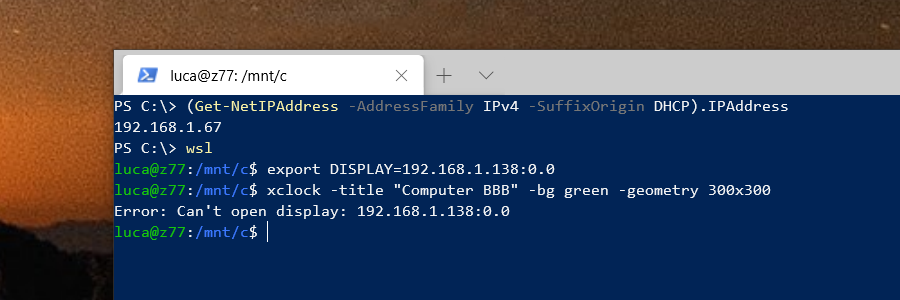
Unlike WSL (Windows Subsystem for Linux) version 1, WSL version 2 (WSL2) has its own isolated network and you cannot readily connect back to X410 running in Windows via TCP/IP connections; Windows Defender Firewall blocks such connections for security reasons.
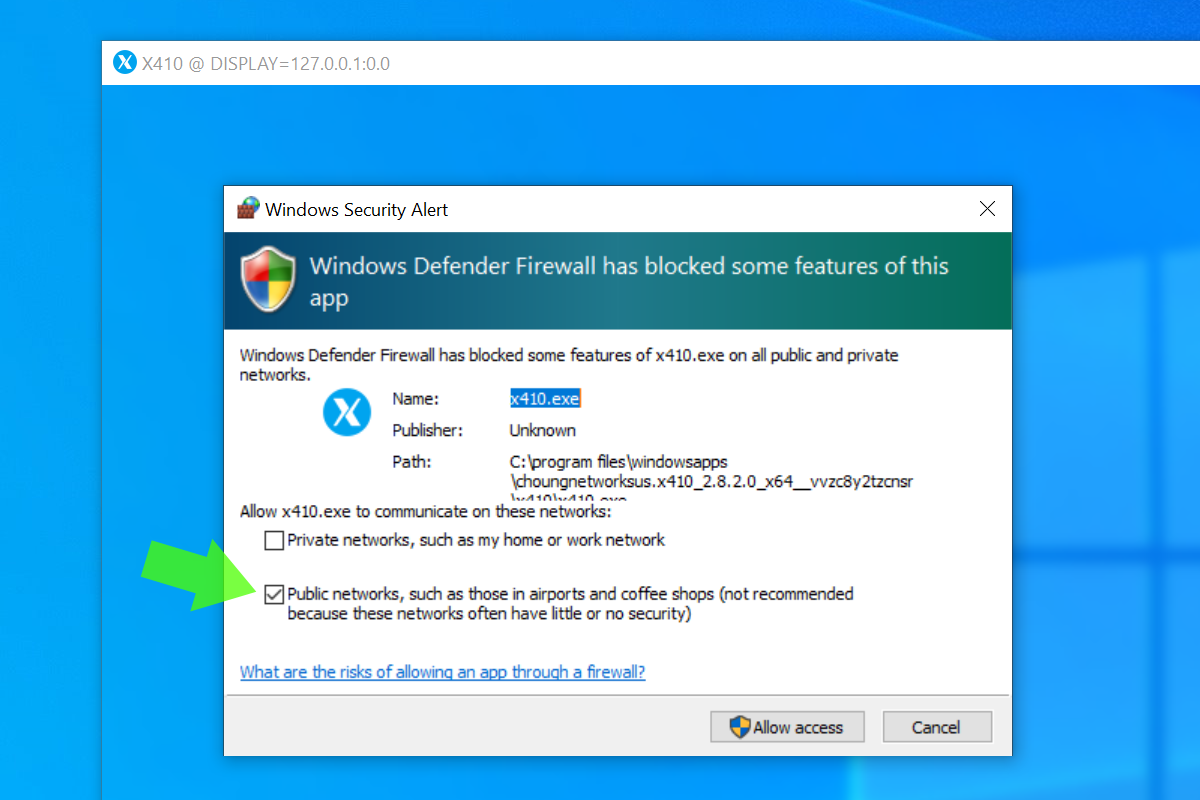
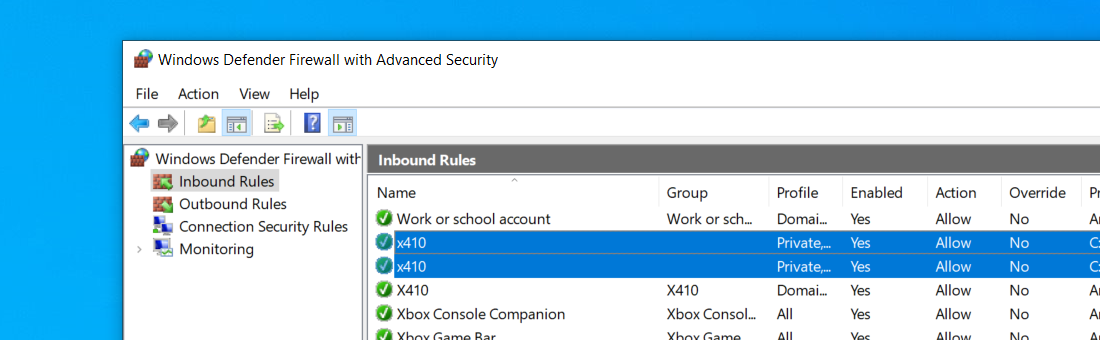
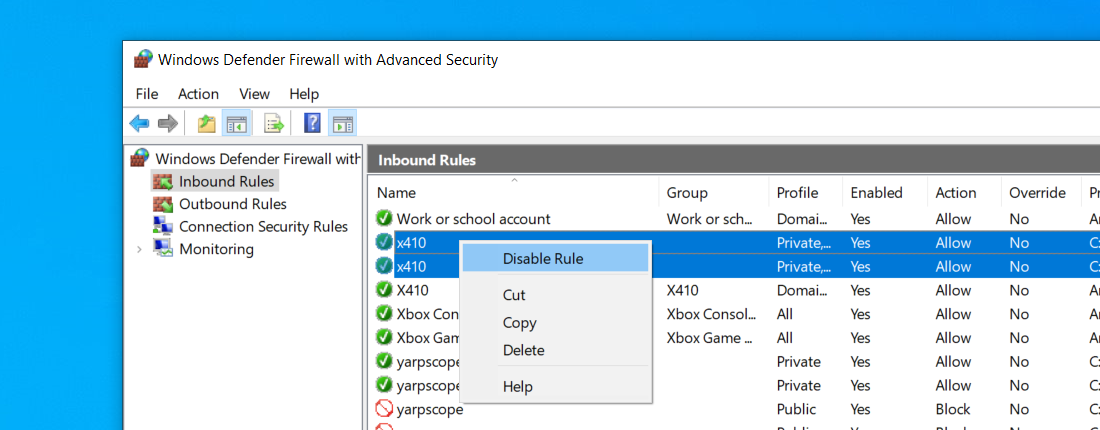
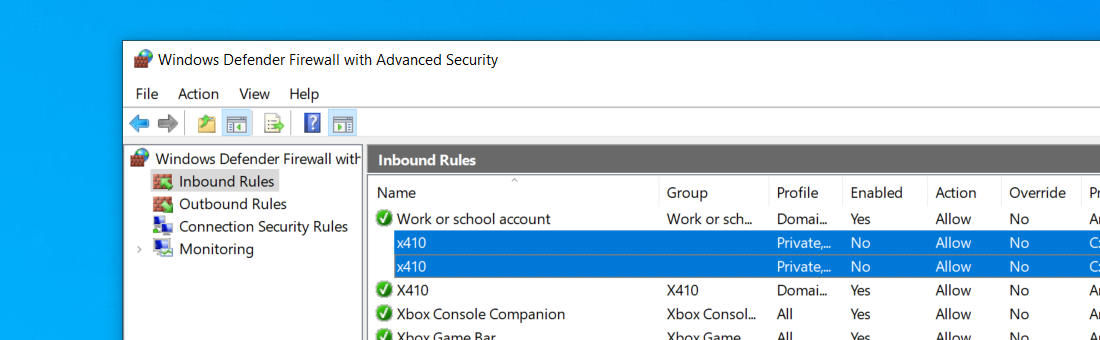
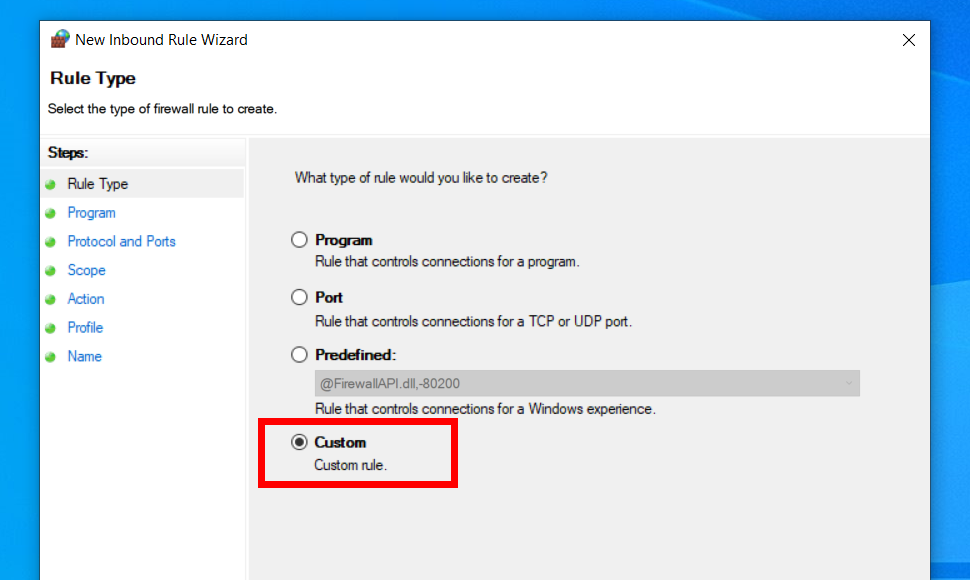
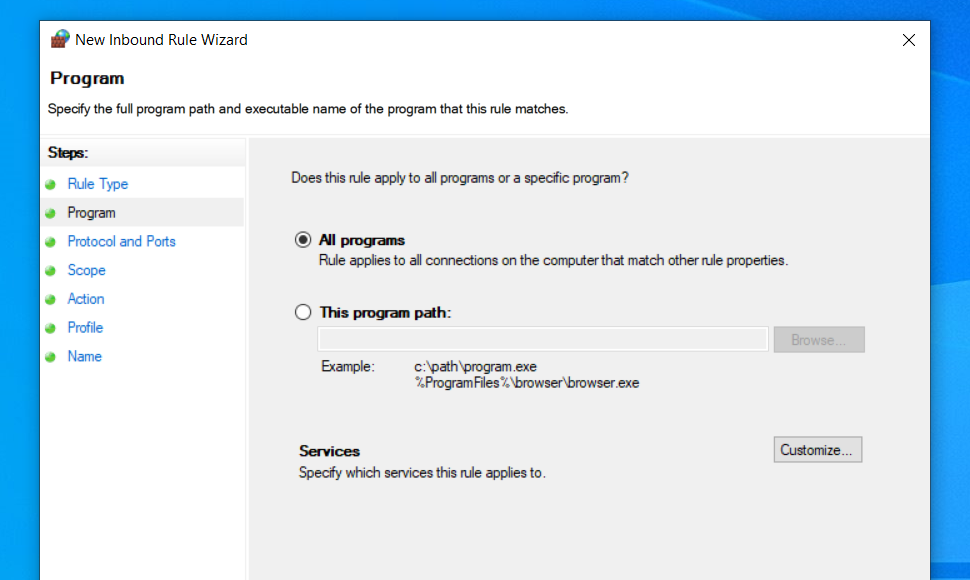
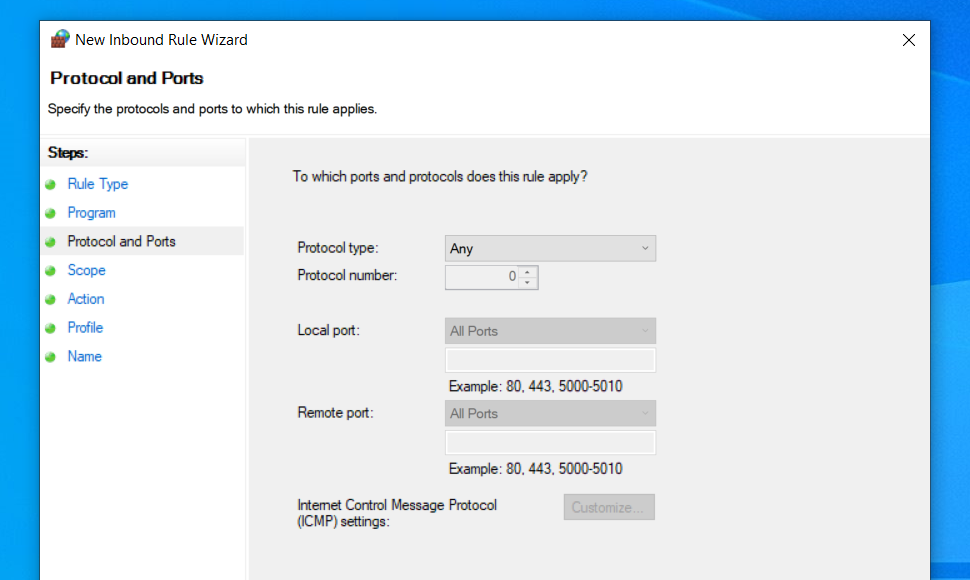
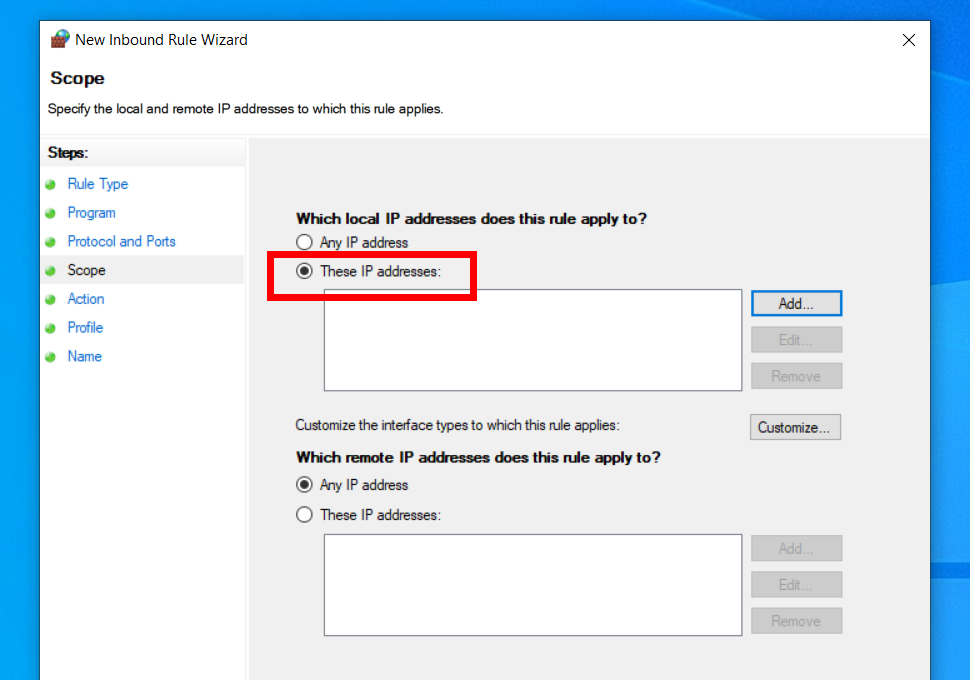
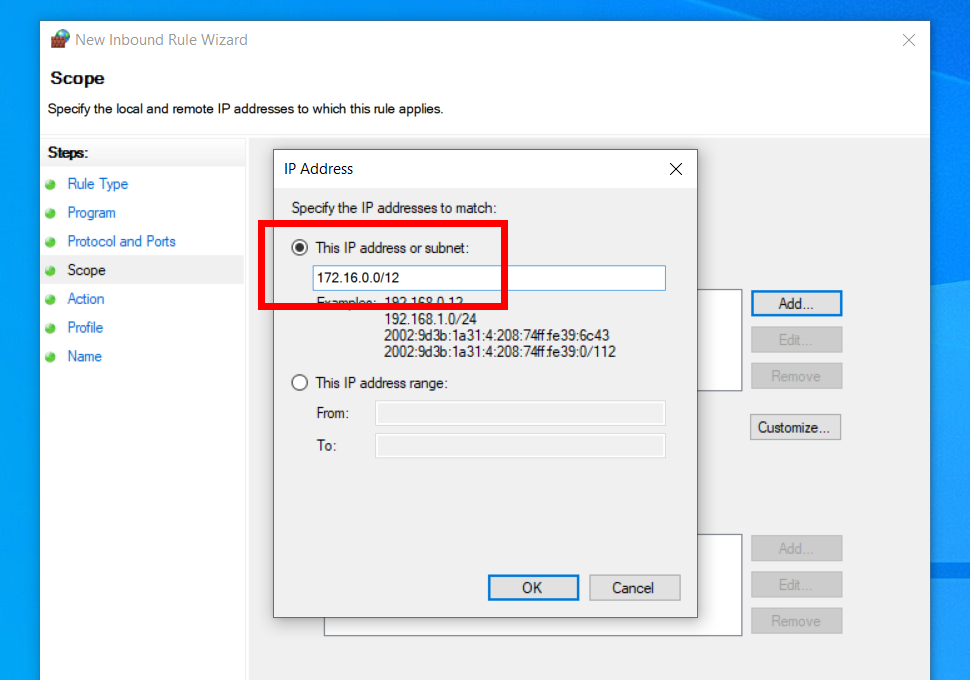
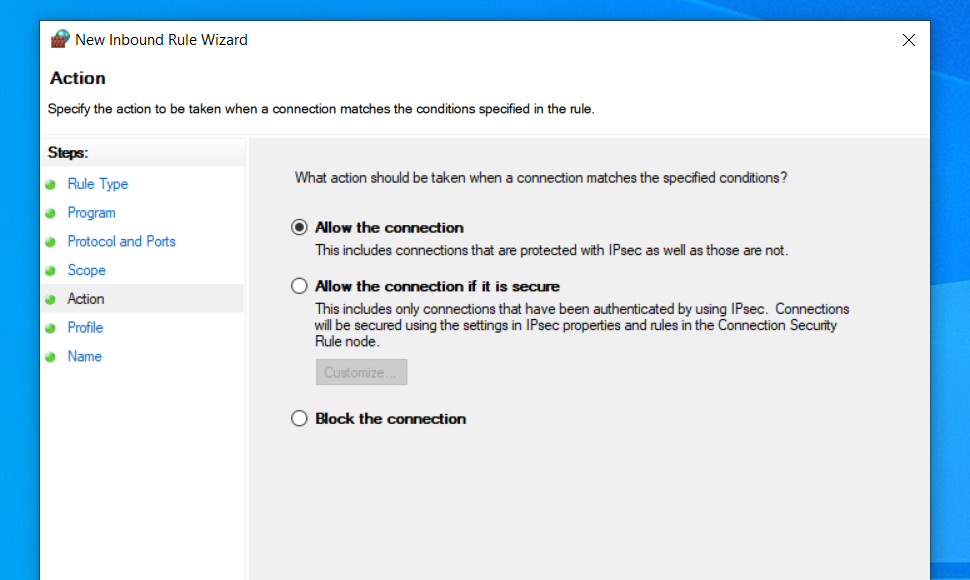
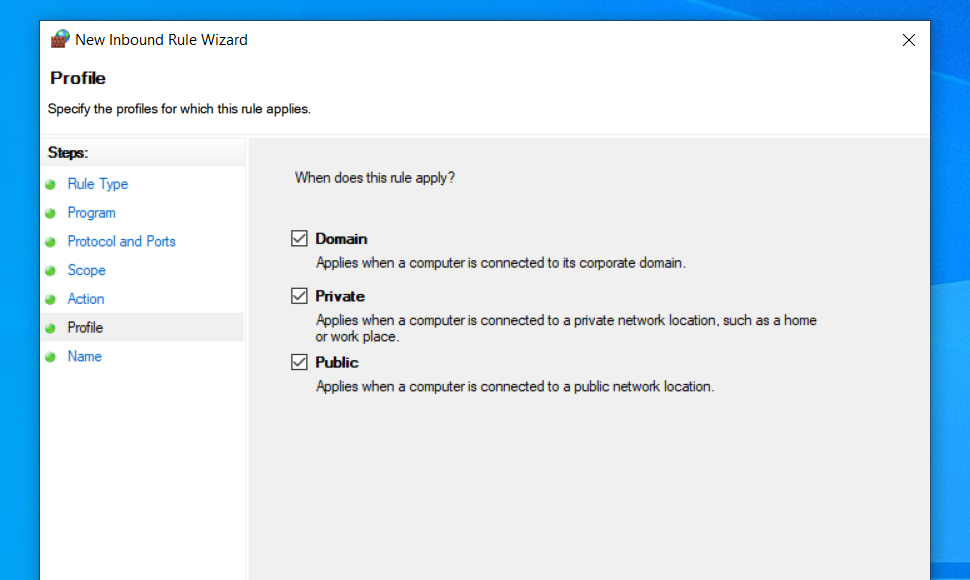
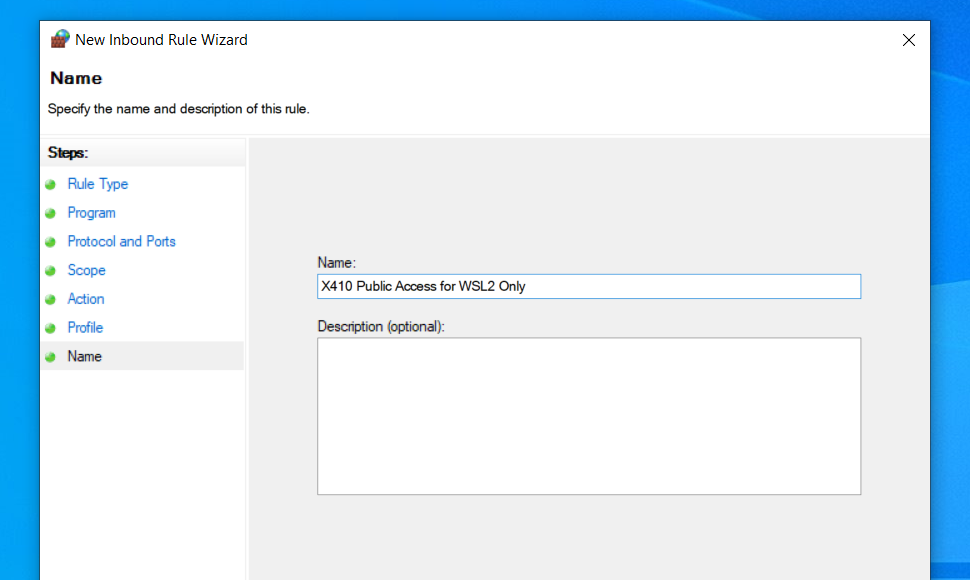
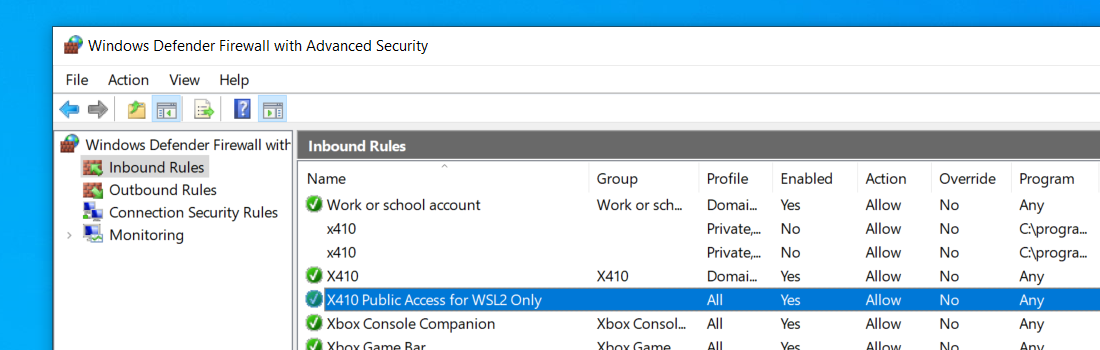
In order to use X410 with those Linux GUI apps running in WSL2, you must enable 'Public Access' option in X410 and allow its inbound public access in Windows Defender Firewall. However, when you grant that public access for X410 in Windows Defender Firewall, any app can forward its GUI output to your X410 even if it's running in a different computer. The following guide shows the steps to prevent such unsolicited connections by adding an inbound rule to Windows Defender Firewall.